Set up secure access to the portal
To ensure the safety of data, the on-site application must be deployed as a web farm when installing the portal. You can find a use case of setting up a web farm in the “Set up a web-farm for Creatio application server” article. Portal access is set up as follows (Fig. 1):
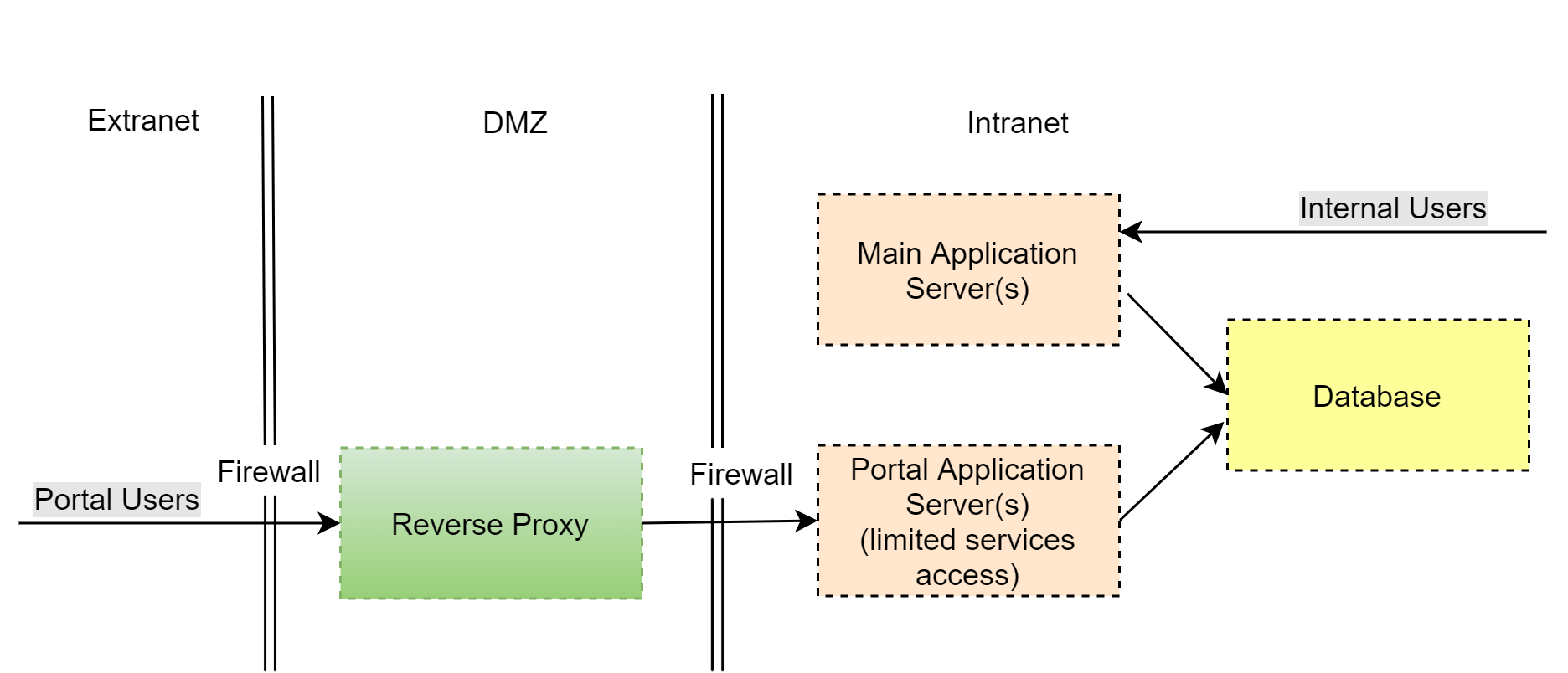
Fig. 1 Typical infrastructure with external network portal access
-
Demilitarized zone (DMZ)
•A reverse proxy server must be the only publicly accessible component in your DMZ.
•The reverse proxy is used to implement the primary network activity logging. You can also configure it to limit access to the configuration files of your application.
•Authorized portal users only have access to those configuration web services that they are expressly allowed to access at the application level.
•During the development process, the access permissions for new web services are configured. Learn more in the “Restricting access to web services for portal users” article.
-
Internal network (Intranet)
•A separate set of application nodes is deployed on the web farm for servicing portal users. This set does not overlap with application nodes for servicing internal users.
•To ensure the operation of the portal application and user application, separate accounts with different access permissions are created in the database.
•The portal application settings deny the system users the ability to log in (“AuthProviders” are disabled, except for portal users). This is required to ensure that only portal users can create sessions from an external network (Extranet).
•Additionally, you can configure external authentication providers to add a second authorization step.
•Portal application nodes, DBMS, and user applications are deployed in separate segments with restricted access.
See also






