The system operations audit log automatically registers events related to user roles modification, access rights distribution, system settings value change and users' authorization in the system.
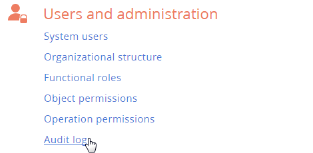
To view the change log, open the system designer by clicking the  button in the top right corner of the application. Click the [Audit log] link in the [Users and administration] block (Fig. 1).
button in the top right corner of the application. Click the [Audit log] link in the [Users and administration] block (Fig. 1).
Fig. 1 Opening the system operations audit log
To be able to view the system operations audit log, you will need to have access to the [View “Audit log” section] system operation, and to be able to view and archive records, you will need to get access to the [Manage “Audit log” section] system operation.
Audit log setup
You can enable and configure the audit log using system settings or by editing configuration files (cloud users will need to contact bpm’online support for this). To enable the audit log using system settings:
1.Open the system designer by clicking the  button at the top right corner of the application window.
button at the top right corner of the application window.
2.Click the [System settings] link in the [System setup] block.
3.Select the [Audit log] folder (subordinate to the [Access rights] folder). This folder contains all system settings that control the audit log. Each type of logged event has a dedicated system setting that enables or disables it.
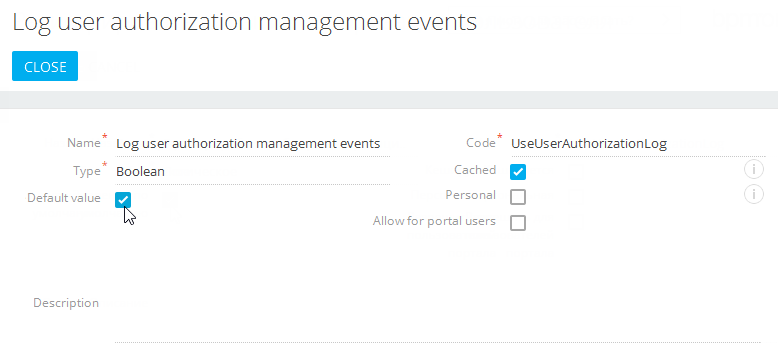
4.To enable the setting, open it and select the [Default value] checkbox. For example, to enable logging of login/logoff events, select the checkbox in the [Log user authorization management events] system setting (Fig. 2).
Fig. 2 Selecting the [Dafault value] checkbox
Note
After disabling an audit log system setting, you may need to restart the Redis session server for the changes to take effect.
Note
If the audit log is enabled on the system configuration file level, the corresponding system setting values will be ignored.
The following event types are registered:
-
Managing users – adding, modifying, and removing system users.
-
Managing organization structure – adding, modifying, and removing organization structure items (user “roles”).
-
Managing user roles – adding users to organization structure items, excluding users from roles.
-
Managing administrated objects – managing types of permissions that can be applied to object.
-
Managing object access rights – modifying access rights to read, modify, and delete operations in an object.
-
Managing access rights to objects for external resources – modifying access rights to objects used for integration between bpm’online and various external services via the OData protocol.
-
Managing access rights to columns – modifying access rights to the object columns.
-
Managing access rights to records – modifying access rights that are assigned to object records. You can enable logging of this event using the [Log entity schema records access rights management events] system setting.
-
Managing access rights to records by default – modifying access rights that are assigned by default to object records.
-
Managing access rights to operations – modifying access rights to the system operations.
-
Managing ranges of IP addresses – modifying or removing ranges of valid IP addresses.
-
Managing system settings – modifying system setting values.
-
User authorization – user authorization attempts (successful or not).
-
Managing audit log – archiving records of system operations audit log.
-
User session – ending user sessions.
Views
The [Audit log] section contains the following views:
-
[Audit log] – the list of the last registered events.
-
[Log archive] – the list of events for which the [Archive log] action was performed. The archived events are stored in a separate table.
Log list
[Event type] – the list of system event types is included in the [Event types] lookup, for example, “User authorization”, “User session”.
[Event date] – date and time of the event start.
[Result] – the list of results of the system events is included in the [Event results] lookup. For example, the attempt of authorization can end with the “Authorization” result, or with the “Authorization denied” result if it fails.
[IP address] – the IP address of the user who performed the operation that resulted in the system event. For example, the IP address of the user who attempted to log in to the system.
[Owner] – the user that performed the operation that resulted in the system event. For example, the name of the employee who attempted to be authorized in the system.
[Description] – the detailed description of the event, for example, “User authorization John Best. IP: 192.168.0.7”. The event description is generated automatically.
Actions
The system operation audit log contains the [Archive log] action that copies the log records to a separate archive table.
Performing the action opens the [Archive parameters] page (Fig. 3) where you can set up parameters for archiving.
Fig. 3 The [Archive parameters] window
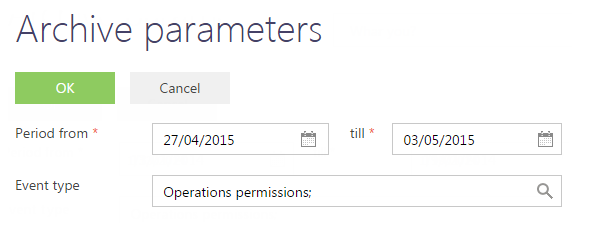
[Period from], [till] – the time period that includes the records to be archived. Only those events whose date falls in the specified range will be archived.
[Event type] – select types of events to be archived. Only those events whose types match the selected ones will be archived. You can select multiple types.
Performing the archiving action is logged as “Access rights audit log”. Once the operation is complete, the system shows the number of the archived records in a message.
See also






