Single Sign-On via AD FS
You can integrate your Active Directory Federation Services (AD FS) instance to manage single sign-on for your members. To do this, perform the setup both in AD FS and Creatio.
This example uses the https://site01.creatio.com/Demo_161215/ Creatio website and http://ADFS01.mysite.com/ADFS/ AD FS website. Replace these URLs with the corresponding URLs of your websites when you perform the actual setup.
The following steps are the general procedure required to set up Single Sign-On in Creatio:
- Download the file that contains integration metadata. Read more >>>
- Perform the setup in AD FS. Read more >>>
- Perform the setup in Creatio. Read more >>>
Download the metadata
- Click the
 button to open the System Designer.
button to open the System Designer. - Click Single Sign On configuration.
- Click
 . This opens a drop-down menu.
. This opens a drop-down menu. - Select "AD FS". This opens the setup page.
- Click Get metadata.
- Save the file to your local machine.
Perform the setup in AD FS
-
Add a new Relying Party Trust to ADFS (Fig. 1).
Fig. 1 Relying Party Trust menu 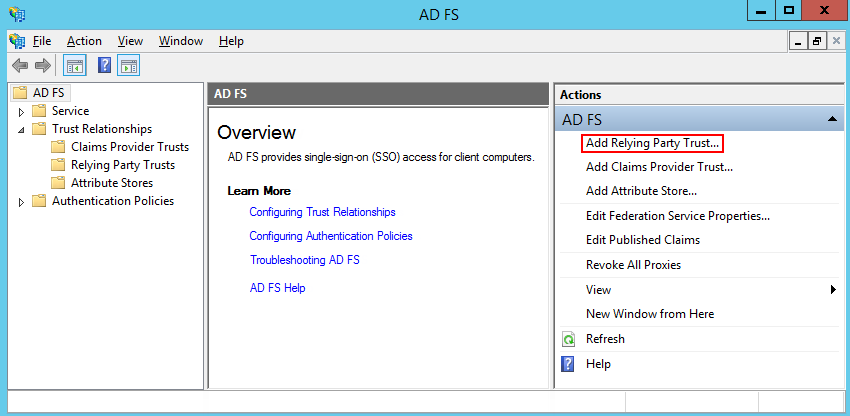
-
Select "Import data about the relying party from file," (Fig. 2).
Fig. 2 Import data about the relying party from file option 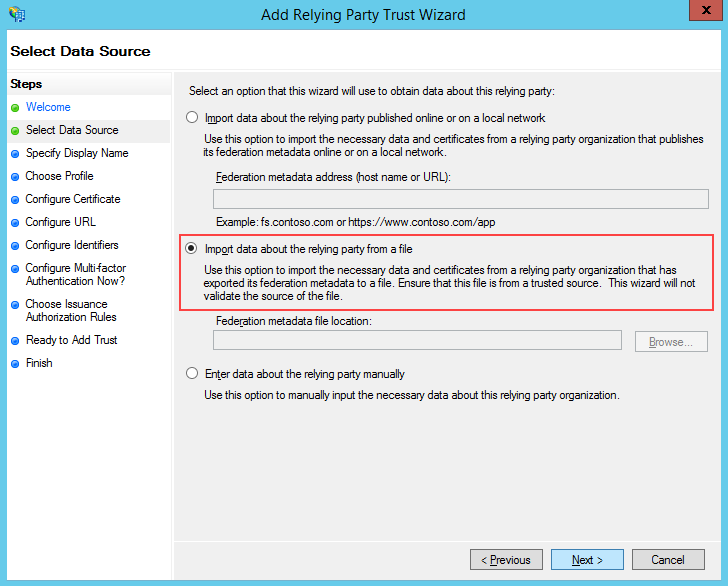
-
Specify the full website address in the "relying party trust identifier" field and click Add (Fig. 3).
Fig. 3 Identifier 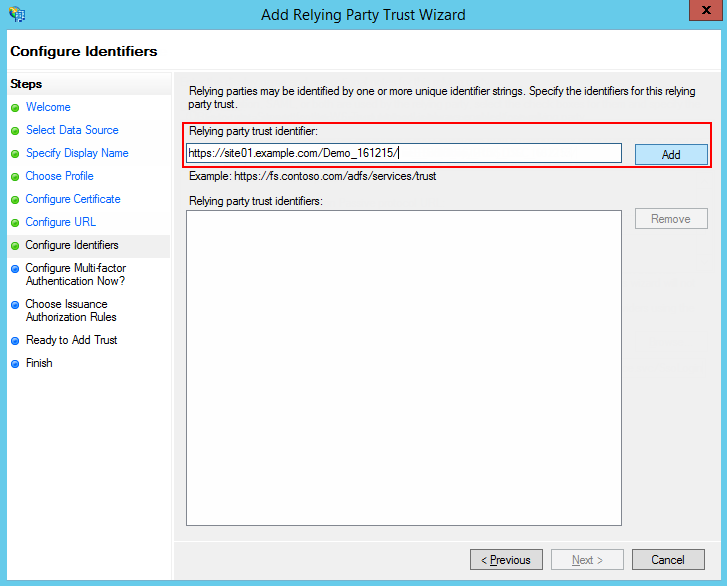 Important
ImportantThe identifier is required to verify the authenticity of a source that requests authentication. The URL must match verbatim, including the "/" at the end.
-
Set up the rest of the parameters according to your security requirements. You can leave default values for test purposes.
-
Click Finish. This opens a window.
-
Click Add Rule and add a new SAML Assertion to SAML Response rule (Fig. 4).
Fig. 4 Add rule button 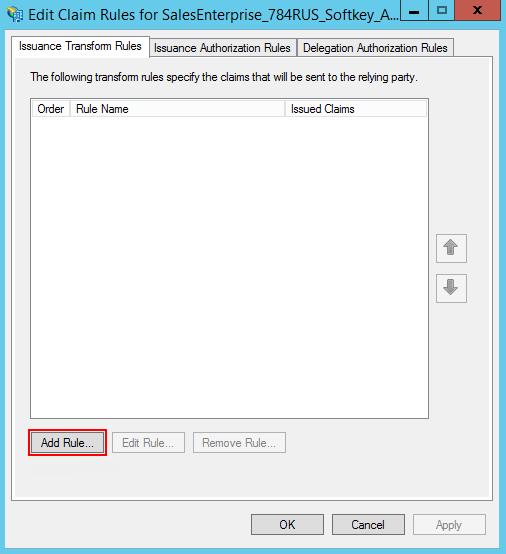 note
noteCreatio will use the data generated based on the new rule to search for users, as well as to update their profiles and roles.
-
Keep the default settings and click Next on the first step of the Rule Wizard. Set up a set of parameters to receive from the user’s data (Fig. 5). In this example, the user’s name and a list of domain groups will be passed via SAML Assertion.
Fig. 5 Rule parameters 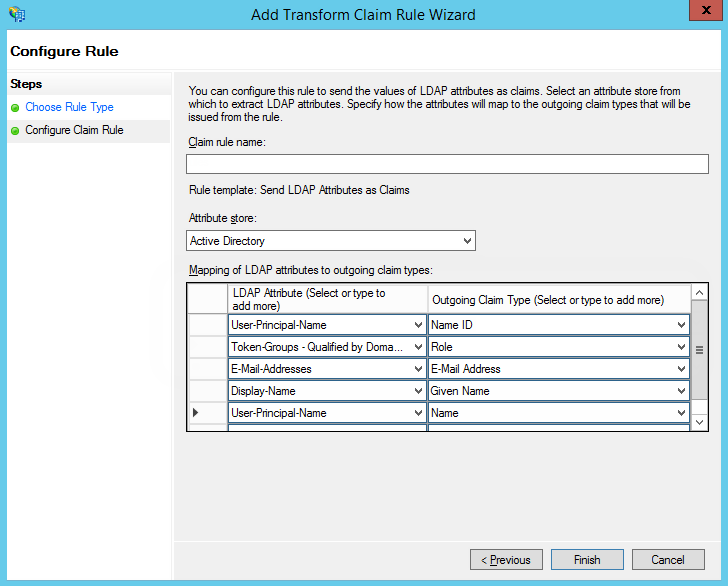
-
Click Save.
-
Open the Trusted Relay settings, go to the Advanced tab, and specify SHA-1 encryption according to the website certificate algorithm.
-
Add the public certificate key on the Encryption tab to set up the SAML encryption (Fig. 6). This step is required only for on-site Creatio.
noteIf you are using Creatio in the cloud, get the public certificate key from the Creatio support service.
Fig. 6 Encryption tab 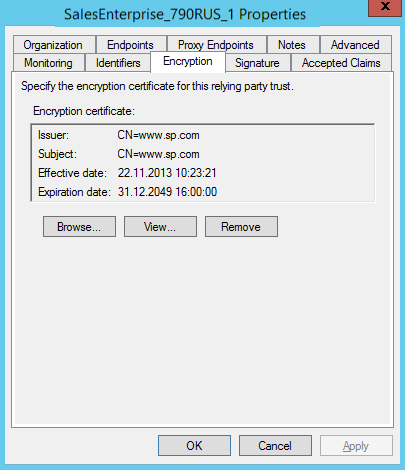
-
Add the logout endpoint and set the following parameters (Fig. 7) on the Endpoints tab:
- Set Endpoint type to "SAML Logout".
- Set Binding to "Redirect".
- Enter
https://site01.creatio.com/Demo_161215/ServiceModel/AuthService.svc/SsoLogoutin the Trusted URL parameter.
Fig. 7 Endpoint parameters 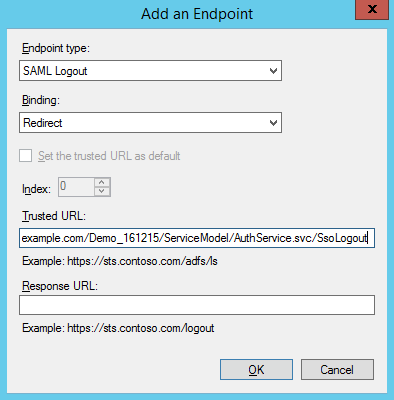
-
Add the Logout Request certificate to the Signature tab (Fig. 8).
Fig. 8 Logout Request certificate 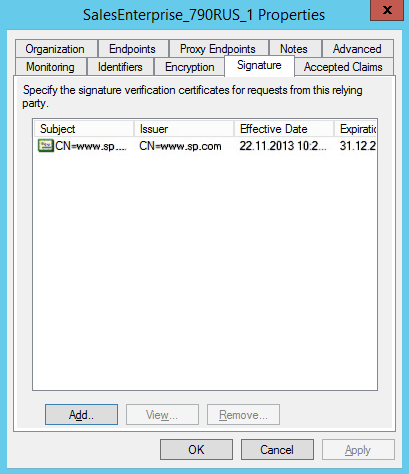
Single Sign-Out needs a certificate to .
Perform the setup in Creatio
Follow these steps to set up single sign-on in Creatio:
-
Click the
 button to open the System Designer.
button to open the System Designer. -
Click Single Sign On configuration.
-
Click
 . This opens a drop-down menu.
. This opens a drop-down menu. -
Select "AD FS". This opens the setup page.
-
Fill out the AD FS tenant URL parameter. Creatio will populate other parameters automatically.
-
Fill out the provider's name to display on the Creatio login page in the Display name field (Fig. 9).
Fig. 9 AD FS settings 
-
Save the changes.
-
Turn on Just-In-Time Provisioning (optional). This mechanism automatically creates the corresponding Creatio user account with data from the identity provider, such as user group, employee name, contact information, etc. For company employees, select the Create and update company employees data when log in (Just-In-Time Provisioning) checkbox and map the fields. For external users, select the Create and update external users data when log in (Just-In-Time Provisioning) checkbox and map the fields (Fig. 10).
Fig. 10 Set up Just-In-Time Provisioning 
-
Define your provider. To do this, specify the provider in the "Default SSO provider" system setting ("DefaultSsoProvider" code) and save the changes.
-
Test whether the provider is working correctly (optional).
Set up SSO authentication for Mobile Creatio
Mobile Creatio lets you log in using the Single Sign-On technology. To set up SSO authentication for Mobile Creatio, turn on the "Use SSO in the mobile app" ("MobileUseSSO" code) system setting.
If the SSO authentication for Mobile Creatio is turned on, the app displays an identity provider page that includes the login and password fields.