Single Sign-On via Cognito AWS
This functionality is available for Creatio 8.0.8 and later.
Creatio can be integrated with any identity provider that supports the Open ID protocol. You can use Cognito AWS portal as a single sign-on point for all your services, including Creatio. To do this, perform he setup both in Cognito AWS and Creatio.
In general, the following steps are required to set up Single Sign-On in Creatio:
- Sign up for Cognito AWS.
- Perform the setup in Cognito AWS. Read more >>>
- Perform the setup in Creatio. Read more >>>
Perform the setup in Cognito AWS
-
Sign in to Aws.Amazon as root user.
-
Click App client list → Create app client.
-
Enter "Creatio" in the App client list field.
-
Click Client secret → Generate a client secret.
-
Enter
[creatioURL]/ServiceModel/AuthService.svc/OpenIdCallbackin Allowed callback URLs where [creatioURL] is the URL of your Creatio instance. -
Enter
[creatioUrl]/ServiceModel/AuthService.svc/OpenIdLogoutCallbackin Allowed sign-out URLs where [creatioURL] is the URL of your Creatio instance. -
Select Email, OpenId, Phone, Profile in the OpenID Connect scopes block.
Fig. 1 OpenID Connect scopes block 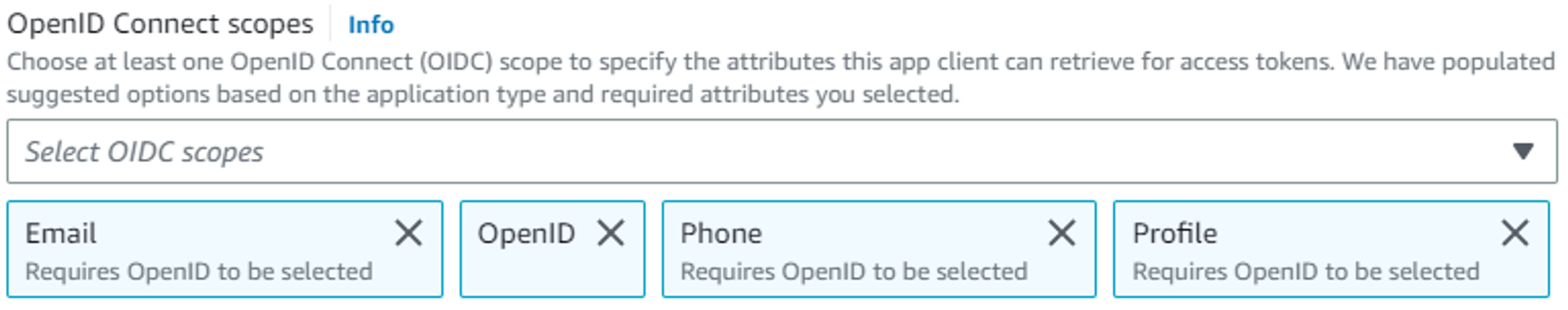
-
Click Create app client.
-
Save the following data from Cognito AWS console to your machine:
- Client ID. Consists of 26 letters and digits. To find this value open the App integration section → App client list.
- Client secret. Consists of 52 letters and digits. To find this value open the App integration section → App clients and analytics block → click the name of your application.
- User pool ID. View the value in the settings of a specific user pool.
- Region. Matches the "Region" parameter in the "User pool ID" value. For example,
User pool ID = cognito-idp.us-east-1.amazonaws.com/us-east-1_123456789, where us-east-1 is the required region. Learn more in Cognito documentation.
Perform the setup in Creatio
If you use Creatio in the cloud, the Open ID authorization is enabled out of the box.
To evaluate Open ID authorization in Creatio on-site, enable the "EnableOpenIDAuth" additional feature. Instructions: Change the status of an additional feature for all users (developer documentation).
Follow these steps to configure single sign-on in Creatio:
-
Click the
 button to open the System Designer.
button to open the System Designer. -
Click Single Sign On configuration.
-
Click
 . This opens a drop-down menu.
. This opens a drop-down menu. -
Select "Cognito AWS." This opens the setup page.
-
Fill out the following parameters:
- Enter the client ID retrieved from Cognito AWS in the Client ID parameter.
- Enter the client secret retrieved from Cognito AWS in the Client secret parameter.
- Enter your provider’s website in the URL parameter. The URL template is as follows
https://[userPoolId].auth.[Region].amazoncognito.com. [Region] and [UserPoolId] are "Region" and "User pool ID" values retrieved from Cognito AWS console, respectively. - Enter the URL of the identity provider’s single sign-on in the Discovery URL parameter. The URL template looks like
https://cognito-idp.[region].amazonaws.com/[userPoolId]/.well-known/openid-configuration. [Region] and [UserPoolId] are "Region" and "User pool ID" values retrieved from Cognito AWS console, respectively. - Enter the URL of the identity provider’s single sign-off in the End session endpoint parameter. The URL template is as follows
https://[userPoolId].auth.[region].amazoncognito.com/logout?client_id={client_id}&logout_uri={redirect_uri}&state={state}. [Region] and [UserPoolId] are "Region" and "User pool ID" values retrieved from Cognito AWS console, respectively.
-
Fill out the provider name to display on the Creatio login page in the Display name field.
-
Save the changes.
-
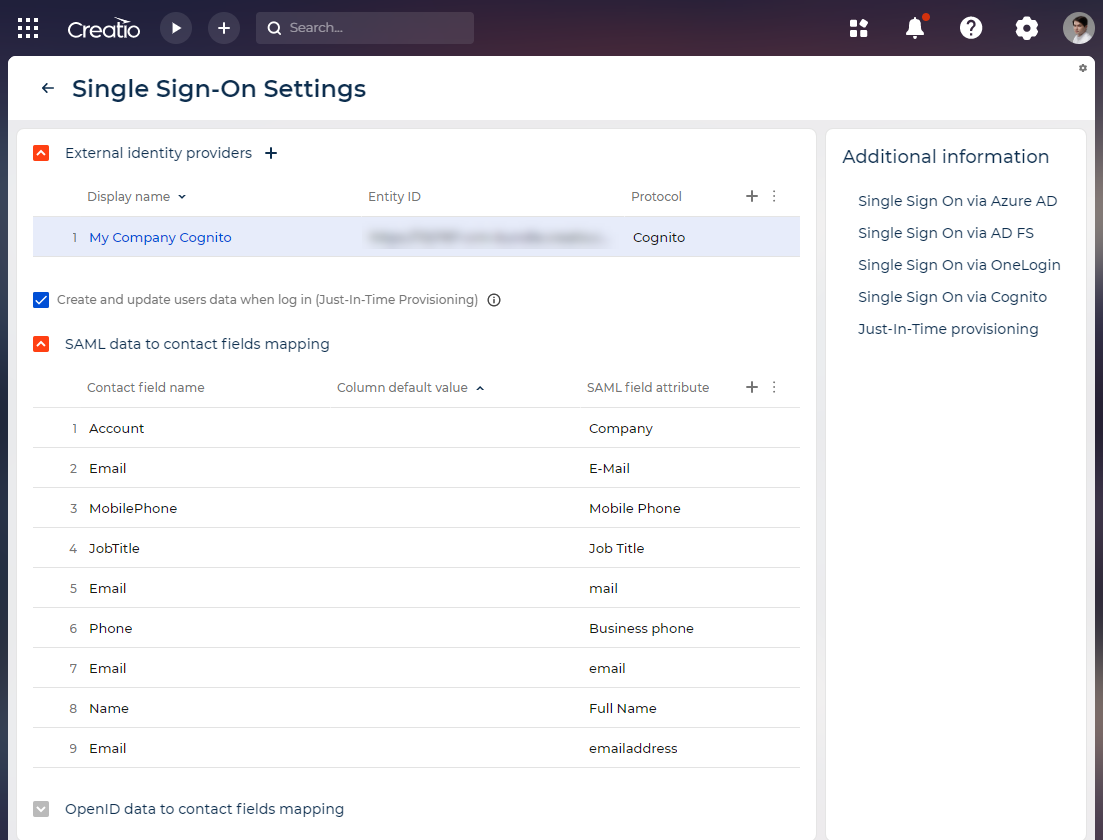
Turn on Just-In-Time Provisioning (optional). This mechanism automatically creates the corresponding Creatio user account that contains data from the identity provider, such as user group, employee name, contact information, etc. To do this, select the Create and update users data when log in (Just-In-Time Provisioning) checkbox and map the fields.
Fig. 2 Set up Just-In-Time Provisioning