You can use OneLogin SSO portal as a single sign-on point for all your services, including Creatio. For this, you need to configure a number of settings both on the OneLogin and Creatio's end.
Settings on OneLogin's end
-
Start the procedure by logging in to OneLogin using an administrator account.
-
Click Apps and select Add Apps. Enter “Creatio” in the search bar and select the Creatio application.
-
If needed, change the value in the Display name field, modify the application icons, or clear the Visible in portal checkbox. These settings affect the way the website is displayed on the OneLogin site.
-
Click Save.
-
Go to the Configuration tab and enter your website domain name in the Creatio site field (Fig. 1). For example, “site01.”
Fig. 1 The website configuration page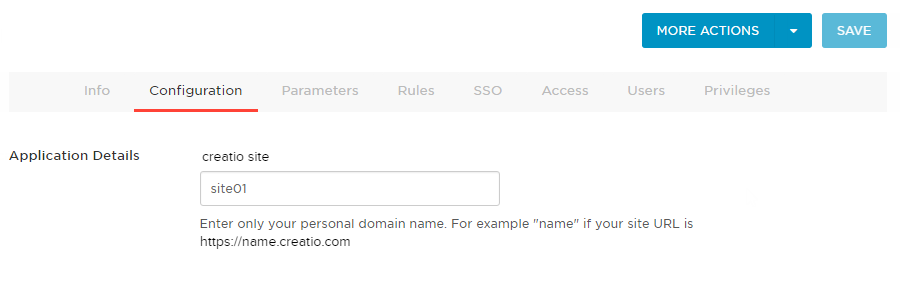
Settings on Creatio's end
If you use Creatio cloud, prepare the setup information according to the instructions below and contact Creatio support to apply the settings.
The single sign-on setup instructions below are intended for on-site customers. We strongly recommend granting Creatio support temporary access to Creatio configuration or performing setup under the guidance of a Creatio support specialist.
Follow these steps to set up single sign-on on Creatio's end:
- Enter the SAML provider settings.
- Set up the SSO authentication parameters.
- Test the basic SSO scenarios.
- Set up Just-In-Time User Provisioning (JIT).
- Set SSO as the default option.
To do this:
- Fill out the SAML provider settings by specifying the data of the SAML identification provider in the saml.config file.
-
Specify your website's FQDN in the Name parameter.
- Specify the IdP settings in the Partner Identity Provider section. You can view these settings in the metadata file.
- WantAssertionSigned – specify “false” if an encryption certificate will not be used during SAML Assertion data exchange.
- SingleSignOnServiceUrl – URL of the identity provider's single sign-on. You can retrieve it from the SAML 2.0 Endpoint (HTTP) on the trusted application page.
- SingleLogoutServiceUrl – URL of the identity provider's single sign-off. You can retrieve it from the SLO Endpoint (HTTP) on the trusted application page.
- WantAssertionSigned – specify “false” if an encryption certificate will not be used during SAML Assertion data exchange.
-
-
Enable the SSO provider in Creatio. To do this, modify the web.config file in the website root folder:
-
Enable using the SSO Auth providers on login:
- SsoAuthProvider – identity provider for the main application.
-
SSPSsoAuthProvider – identity provider for the customer portal.
You can enable one or both providers.
-
Specify which identification provider from the saml.config file to use in Service Provider initiated SSO scenarios by default. In the web.config App Loader, specify the PartnerIdP parameter value from the Issuer URL string in the saml.config file, such as:
- Set SSO as the default option upon login. To do this, specify the Login/NuiLogin.aspx?use_sso=true resource in the web.config App Loader.
- Enable redirection to the identity provider when going to the website root:
- Enable redirection to the identity provider if no user session is available:
-
-
Test the Identity Provider (IdP) initiated SSO basic scenario to make sure the settings are correct:
-
Navigate to the trusted IdP applications page. The default link is https://sts.contoso.com/adfs/ls/idpinitiatedsignon.aspx.
-
Authorize.
-
Navigate to Creatio with the IdP authorization results.
Test the settings in the IdP initiated scenario before setting SSO as the default option on Creatio's end. Make sure Creatio has an active user account whose login matches the NameId passed by the Identity Provider before starting the test. If there is no such account, the SSO setup process will not finish since it will be impossible to match the domain user to a Creatio user. After you successfully log in via SSO, proceed to further setup.
-
- Set up Just-In-Time User Provisioning (JIT). The Just-In-Time User Provisioning functionality complements the single sign-on technology. It enables not only creating a user on the first login to Creatio but also updating the contact page data with the data received from the identification provider on every login. Learn more: Just-In-Time User Provisioning.
- Add the JIT settings to web.config file in the Creatio root folder:
The user type is defined by the page they use to log in. If the Identity initiated scenario is used to log in, specify the DefUserType value:
-
General – general user.
-
SSP – portal user.
-
-
Map the SAML Assertion fields to Creatio columns using the SAML field name converter to contact field name lookup. You need this to ensure Creatio populates the contact fields correctly when creating new users via Just-In-Time User Provisioning. If the field is empty or disabled in the identity provider data, you can fill it out with the value specified in the Default value field of the lookup. Upon the next login, Creatio will populate the contact fields specified in the lookup with either the values received from the provider or with the current default values.
- Add the JIT settings to web.config file in the Creatio root folder:
-
Set SSO as the default option upon login. We recommend following this step only after you finished the previous steps successfully and made sure the SSO works correctly. This step will enable the Service Provider (SP) initiated SSO. The standard Service Provider (SP) initiated scenario is as follows:
- The user navigates to Creatio, they have no active sessions on the site.
- They are redirected to the IdP where they authorize.
- They are redirected back to Creatio with the IdP authorization results.
To set the SSO provider as the default option:
-
Enable Single Log Out in the web.config file in the Terrasoft.WebApp folder:
-
Select the Default value checkbox in the “SSO in mobile application” (“MobileUseSSO”) system setting to use the Single Sign-On in the mobile application.