Use OAuth 2.0 protocol to securely authorize third-party applications and web services you integrate with Creatio. This technology does not pass Creatio logins and passwords to third-party applications. OAuth 2.0 also lets you restrict Creatio permissions for the integrated applications.
Install and set up the Identity Service
You can install and set up the Identity Service using IIS or, alternatively for Creatio version 8.0.8 and later, using Docker:
- Install and set up the Identity Service using IIS
- Install and set up the Identity Service using Docker
Install and set up the Identity Service using IIS
Deploy the database and Creatio application servers before installing and configuring the Identity Service. To install the Identity Service using IIS:
- Access the Creatio application server.
- Install additional components.
For Creatio version 8.0.7 and earlier
For Creatio version 8.0.8 and later
- Restart the IIS.
- Navigate to the Creatio install file folder, find the IdentityService.zip archive, and unzip it.
- Add the Identity Service application pool to the IIS.
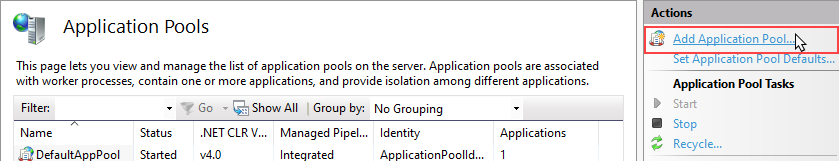
- Go to the Application Pools section in the Connections area of the IIS management window.
- Select Add Application Pool… in the Actions area.
Fig. 1 Add the pool to the IIS
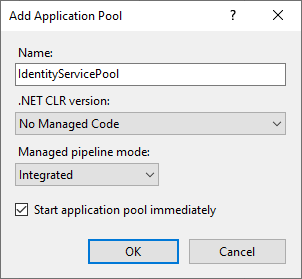
- Specify the pool name in the pool settings window, for example, “IdentityServicePool.” Set the .NET CLR Version field to “No Managed Code.”
Fig. 2 Set up the Identity Service pool
- Set up access to the application pool:
- Right-click the newly-created pool. Select Advanced Settings… in the context menu.
- Specify the user with Identity Service directory access permissions in the Identity field of the newly-opened window.
- Create a new Identity Service site in the IIS.
-
Click Sites on the IIS control panel and select Add Website from the context menu.
-
Specify the site name, the pool and the path to the Identity Service root directory.
Fig. 3 Set up the site in the IIS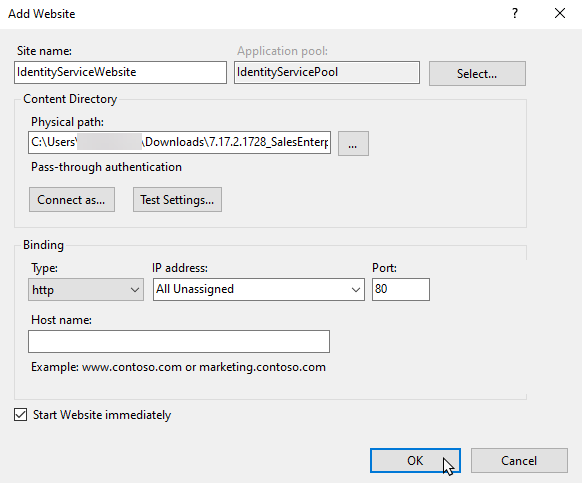
-
-
Connect the site to your Creatio DBMS. To do so, edit the appSettings.json configuration file in the Identity Service root directory:
-
Set the “DbProvider” parameter to “MsSqlServer” or “Postgres.”
-
Specify the connection string in the “MsSqlConnection” or “PostgresConnection” setting. We recommend using the same connection string you specified in Creatio. The user that connects to the database must have permissions to create and update the tables.
-
-
Set up the Identity Service system user. To do so, specify the unique ClientId, ClientName, and ClientSecret values in the “Clients” block of the appSettings.json configuration file. The file is located in the Identity Service root catalog. Creatio and the Identity Service will use these values to interact with each other. All parameters support uppercase and lowercase letters, numbers, and special characters, for example, brackets or punctuation marks.
Recommended parameters:
ClientId — 16 characters.
ClientSecret — 32 characters.
ClientName — any number of characters.
“Clients” block setup example: - Switch the Identity Service to HTTPS. The setup process is similar to switching Creatio to HTTPS. Read more: Switch Creatio website from HTTP to HTTPS.
- Enable the Identity Service logging.
- Navigate to the Identity Service directory, open the web.config file, and set the “stdoutLogEnabled” parameter to “true.”
- Specify where you would like to store the Identity Service logs in the file's “stdoutLogFile” parameter.
- Open the appsettings.json file in the Identity Service root directory and configure the log level:
Install and set up the Identity Service using Docker
Deploy the database and Creatio application servers before installing and configuring the Identity Service.
To install the Identity Service using Docker:
- Navigate to the Creatio install file folder, find the IdentityService.zip archive, which includes the Dockerfile-OAuth file for IdentityService, and unzip it.
- Connect the site to your Creatio DBMS. There are three ways to do this:
- Edit the appSettings.json configuration file in the Identity Service root directory before building.
- Edit the Dockerfile-OAuth file and add environment variables using the ENV directive. For example, specify ENV DbProvider=Postgres, which will set the DbProvider parameter to “Postgres” when the container starts.
- Specify the environment variables when running the container. For example, run the container as follows: docker run --env=DbProvider=Postgres.
-
Set the “DbProvider” parameter to “MsSqlServer” or “Postgres.”
-
Specify the connection string in the “MsSqlConnection” or “PostgresConnection” setting. We recommend using the same connection string you specified in Creatio. The user that connects to the database must have permission to create and update the tables.
-
Set up the Identity Service system user. To do so, specify the unique ClientId, ClientName, and ClientSecret values in the “Clients” setting. Creatio and the Identity Service will use these values to interact with each other. All parameters support uppercase and lowercase letters, numbers, and special characters, for example, brackets or punctuation marks.
Recommended parameters:
ClientId — 16 characters.
ClientSecret — 32 characters.
ClientName — any number of characters.
“Clients” setting setup example: - Configure RedisConnection or leave it blank if configuring security settings for the IdentityService configuration is not required. The RedisConnection setting stores the machineKey value to prevent spoofing during runtime.
- Build the Docker image after configuring using the command:
- Run the container using the following command:
- Switch the Identity Service to HTTPS. Before configuring HTTPS, obtain a digital certificate from the certification center in PFX format. To switch IdentityService to HTTPS, run the docker container as follows:
http_port_number is a port number. Docker will serve the HTTP version of IdentityService on this port.
https_port_number is a port number. Docker will serve the HTTPS version of IdentityService on this port.
{Certificate Password} is the password for the openssl.pfx certificate.
{Certificate Path} is the path to the openssl.pfx certificate.
- Enable the Identity Service logging.
- Navigate to the Identity Service directory, open the web.config file, and set the “stdoutLogEnabled” parameter to “true.”
- Specify where you would like to store the Identity Service logs in the file's “stdoutLogFile” parameter.
- Open the appsettings.json file in the Identity Service root directory and configure the log level:
Update the Identity Service using IIS
The Identity Service archive is provided with the Creatio distribution. Please update the Creatio application before updating the Identity Service. To ensure that all required components are up-to-date:
- Access the Creatio application server.
- Install .NET 6 Runtime. You can download it from the Microsoft website.
- Install .NET 6 Hosting Bundle. You can download it from the Microsoft website.
- Restart the IIS server.
To update the Identity Service:
- Navigate to the Identity Service application folder and back up the files. For example, copy the directory to a backup location.
- Back up the database of the current version of Identity Service. Learn more: Creating database backup.
- Stop the Identity Service pool and application in the IIS.
- Navigate to the Creatio install file folder, find the IdentityService.zip archive, and unzip it.
- Replace all files In the Identity Service application folder with the unzipped files.
- Set up the Identity Service as described in Install and set up the Identity Service using IIS.
- Start the Identity Service pool in the IIS.
-
Verify that the Identity Service is running by opening [your-identity-app]/.well-known/openid-configuration, where [your-identity-app] is the URL of your Identity Service application.
As a result, the Identity Service for Creatio will be updated. If you encounter any issues, please contact Creatio support for assistance.
Set up the Identity Service integration on Creatio's end
- Enable the OAuth 2.0 integration in Creatio. To do so, execute this script in your Creatio database. Use it for both Microsoft SQL and PostgreSql.
- Fill in the system settings in the “OAuth 2.0” group:
- “Authorization server Url for OAuth 2.0 integrations” (“OAuth20IdentityServerUrl” code) — the IdentityServer URL, for instance, http://isEnpointExample.
- “Client id for OAuth 2.0 integrations” (“OAuth20IdentityServerClientId” code) — the Identity Service user ID you specified in the “ClientId” parameter of the appSettings.json file when setting up the IdentityServer.
- “Client secret for OAuth 2.0 integrations” (“OAuth20IdentityServerClientSecret” code) — the Identity Service user's secret key you specified in the “ClientSecret” parameter of the appSettings.json file when setting up the IdentityServer.
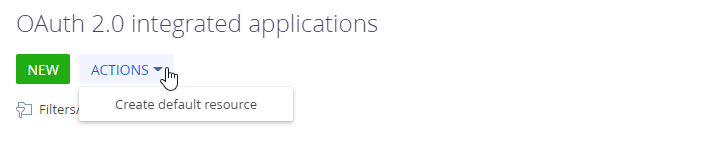
- Create a default resource. You only need to perform this action once when setting up the Identity Service integration.
- Click
 to open the System Designer.
to open the System Designer. - Open the OAuth 2.0 integrated applications section.
- Select Create default resource in the Actions menu.
Fig. 4 Add a default resource
- Click
This will create a default resource record with your Identity Service account details.
Set up the OAuth 2.0 authorization
Once you install the Identity Service and connect it to Creatio, add a client record for each application you are going to authorize with OAuth 2.0. To do so:
- Click
 to open the System Designer.
to open the System Designer. - Open the OAuth 2.0 integrated applications section.
- Click New.
- Fill in the client parameters for the relevant application on the newly-opened page.
- Name — the title that the integration list and the logs will use.
- Application URL — the URL of the integrated application or the web service.
- Description — the purpose of the integration.
- Active — enables and disables the integration.
-
System user — the Creatio user with sufficient permissions for this integration. We recommend permitting this user to only read and edit the fields the integrated application or the web service need to change. For example, if you are integrating a web service that passes the currency exchange rates to Creatio, grant permissions to only read and edit the Rate and Start fields of the Currency lookup.
Creatio automatically populates the client account details (the ID and the secret).
Fig. 5 Set the client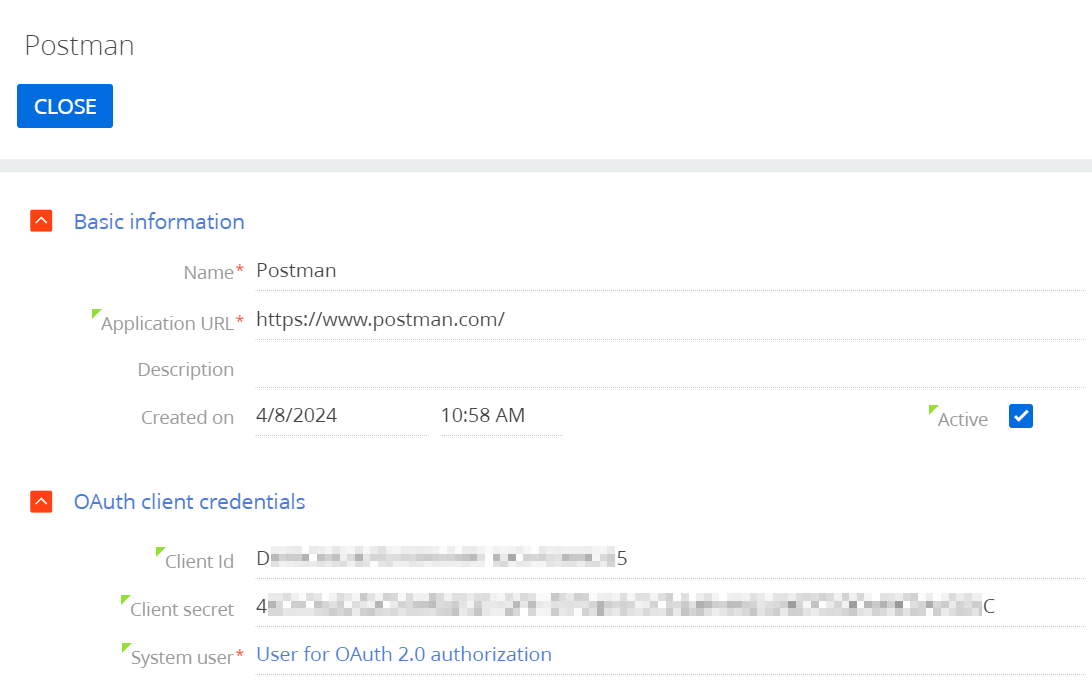
- Save the record.
- Repeat steps 3-6 for all applications you need to authorize with OAuth 2.0.